
Cyber Security Trends: 7 types of cyber security trends provide protection on your computer or electronic devices. Cyber security is far to your system from authorised access by humans or non-humans.
Cyber security is in simple words protecting your computer or system from unauthorised access or hackers. Cyber security is the safe personal and professional information on mobile devices, tablets, computers, laptops, or other electronic devices.
Furthermore, Cyber security is to protect your data or information saved on PC or any electronic devices connected through the internet against unauthorised access. This is the main disadvantage of the Internet or Digital Technology. In this blog, we will explore what is cyber security, and 7 types of cyber security.
What Is Cyber Security?

Mainly, That is providing protection from cyber attacks on hardware, software, and data.
All information, hardware and software are interconnect or through an internet connection.
The security system is very complex. Cyber attackers target a user’s personal information, credit card numbers, Account bank details, name, address, national identification number, etc…
Strong cyber security provides strong protection against cyber attacks and saves your personal and professional information. Cyber attacks are also know as digital attacks.
Optimity Logics is also an IT (Information Technology) Company. That described the 7 types of cyber security trends 2023. So, without wasting time let’s get Started!!!
Types Of Cyber Security
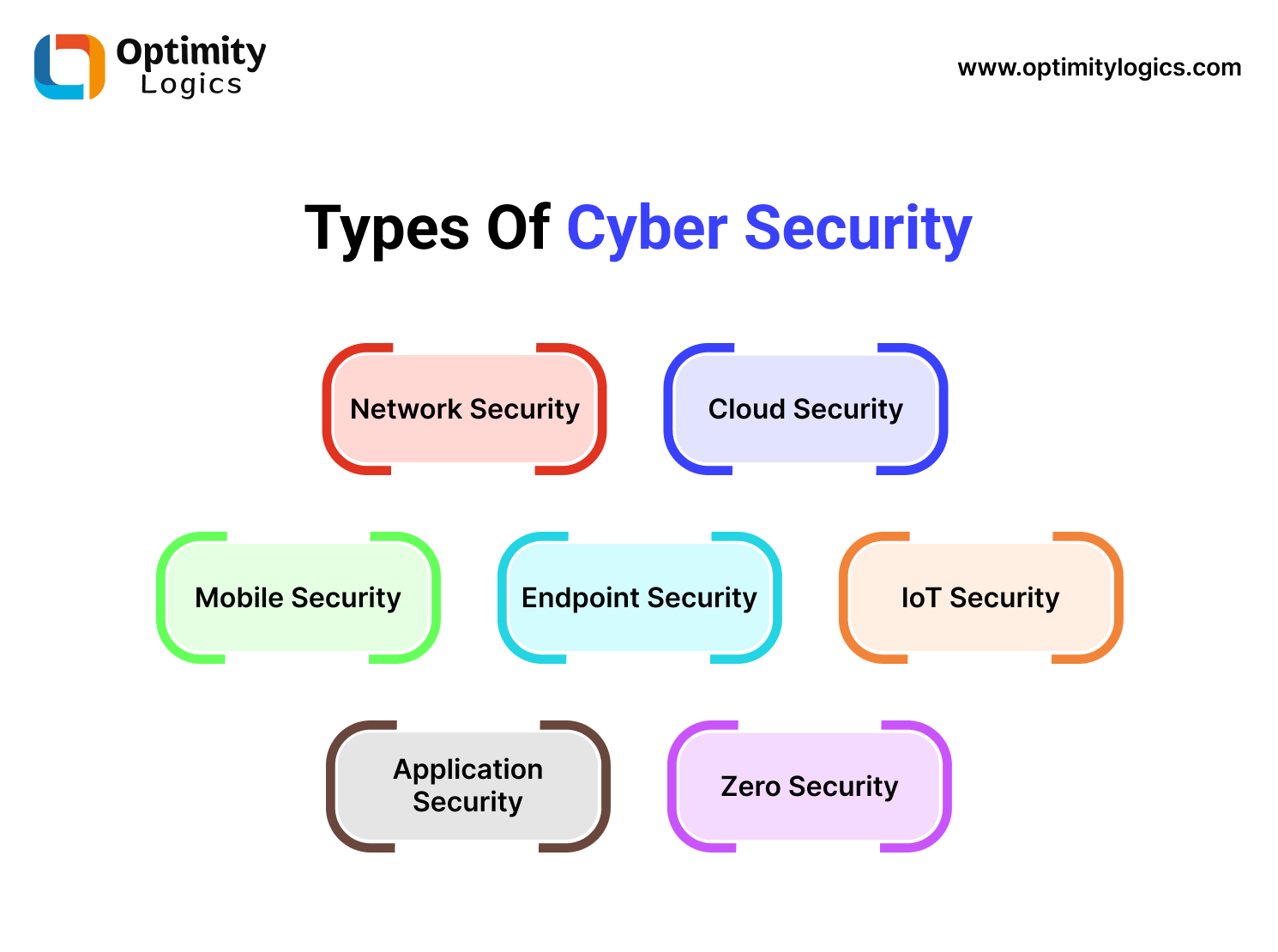
Cyber security is divided into 7 parts. Optimity Logics explores all parts of cyber security. So, stick with us and read on.
Network Security
Most attacks occur on the network or the internet. So, network security is designed to specifically block these attacks. Network security is any activity designed to protect the usability and integrity of your network and data.
Moreover, network security includes both hardware and software technologies. It targets a variety of threats.
Also, Network security is stopping them from entering or spreading on your network. Effective network security manages access to the network.
Cloud Security
Cloud security is also known as cloud computing security. While many cloud providers offer security solutions, these are often inadequate for the task of achieving enterprise-grade security in the cloud. The third-party solution is important to save against information and targeted attacks in cloud environments.
Cloud computing is a collection of procedures and technology designed to address external and internal threats to business security.
Endpoint Security
First of all, Endpoint is a virus that protects your system or computer. That helps detect a virus on devices. This is traditionally includ in viruses. It manages anti-virus software.
The zero-trust security model prescribes creating micro-segments around data wherever it may be. With endpoint security companies can secure end-user devices such as desktops and laptops with data and network security controls.
Mobile Security
Mobile security is the strategy use to protect any wireless devices. Like a smartphone, tablet, laptop, etc…
So, Secure mobile access is important for enterprise cyber security. A lot of mobile devices are use worldwide. And in the latest COVID times companies provide remote work, data, applications, and systems that they access are at increased risk of compromise by interface devices.
IoT Security
The Internet Of Things (IoT) keeps your system safe. It also exposes organisations to new threads. IoT security can be understood as a cyber security strategy and protection that safeguard against the possibility of cyber attacks.
Furthermore, IoT security protects this device with the discovery and classification of the connected devices, auto-segmentation to control network activities, and using IPS as a virtual patch to prevent exploits against vulnerable IoT devices.
Application Security
Web applications, like anything else directly connected to the Internet. That process is the development, addition, and testing of the application that protects the data against unauthorised access and modifications. Application security also prevents bot attacks that can be stopped.
Additionally, Application security includes some examples like Firewalls, antivirus systems, and data encryption.
Zero Trust
Zero trust is a cyber security framework. That is to help protect data and get a smart paper. That is a strategic approach to cyber security that secures an organisation by eliminating implicit trust and continuously validating every stage of digital interactions.
That is identifying humans and robots (non-human) identification needs strong authentication. There are some examples of zero trust like requiring a user to scan their fingerprint or confirm PIN or OTP sent to a mobile device.
Conclusion
Most people use technology and convert digitally. So, all over the world most used mobile devices at this time. It is the advantage of the electronic or digital world.
But, the most important thing is to save or protect your data and personal information. Cyber security provides protection against unauthorised access users or Non-user. So, Optimity Logics tries to simplify 7 types of cyber security or data protection. If you have any questions, feel free to contact our experts.












